iShredder

Gracias por
descargar iShredder Android
Un último paso...
Introduce tu correo electrónico para recibir el enlace de descarga y las
instrucciones de instalación por email.
Principales razones para
elegir iShredder
Eliminación irreversible
Evita que se recupere información sensible. iShredder™ elimina archivos de forma tan segura que ni las herramientas profesionales de recuperación pueden restaurarlos.
Algoritmos de eliminación certificados
Desde DoD 5220.22-M, NIST SP 800-88, BSI TL-03423, entre otros — iShredder™ utiliza algoritmos reconocidos por gobiernos y fuerzas armadas.
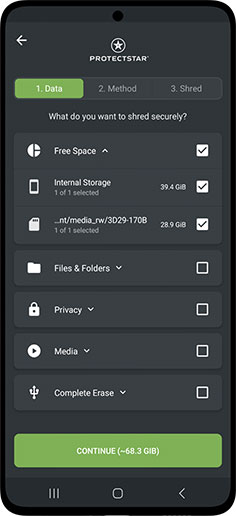
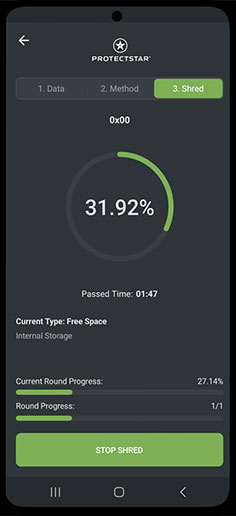
Tres pasos para el éxito
Selecciona los datos a eliminar, elige el algoritmo de borrado y confirma con un clic. Tus datos desaparecerán de forma segura.
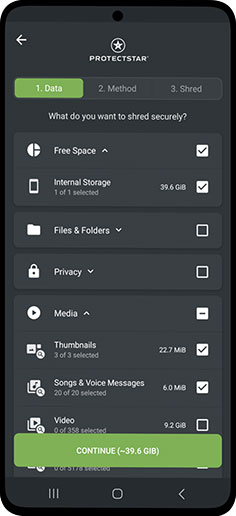
Limpieza de archivos temporales
iShredder™ también elimina cachés ocultos, registros y otros residuos. Libera espacio y evita rastros innecesarios.
Ideal para vender tu dispositivo
Nadie debería acceder a tus fotos, contraseñas u otra información. Con iShredder™, puedes entregar tu dispositivo con total tranquilidad.
Informes y documentación de eliminación
iShredder™ genera un informe detallado por cada acción — ideal para empresas que requieren documentación conforme al RGPD.
Eliminación segura
de nivel militar
iShredder™ es el destructor de datos más popular para iOS, Android, Windows y Mac. La app es adecuada tanto para principiantes como para profesionales que buscan eliminar datos de forma segura. Incluye informe de eliminación.
iShredder™ elimina con estándares internacionales de seguridad militar tan rigurosos que es utilizada por departamentos de defensa y agencias gubernamentales.
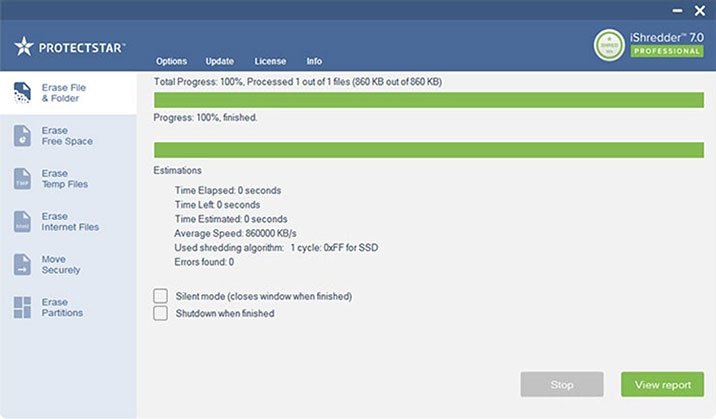
Eliminación irreversible en tres pasos
Por ejemplo, si eliminas manualmente archivos como documentos o fotos, estos aún pueden recuperarse desde el espacio libre del dispositivo hasta que se sobrescriban con algoritmos seguros.
En solo tres pasos, tus archivos o espacio serán sobrescritos con estándares de seguridad patentados, imposibilitando su recuperación:
Selecciona los datos que deseas eliminar
Elige entre más de 20 métodos de eliminación

Comienza a eliminar con un solo clic
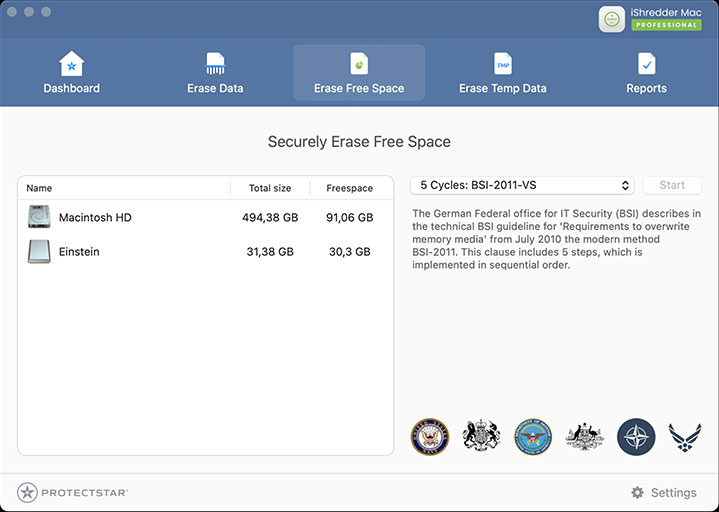
Eliminar no siempre significa borrar
Incluso después de “eliminar” o “formatear”, gran parte de tus archivos puede recuperarse. iShredder™ te muestra qué restos quedan en el espacio libre y los elimina para que nadie pueda reconstruirlos.
Usa la función “Borrar espacio libre de forma segura” de iShredder™ para sobrescribir el espacio libre e impedir la recuperación de datos previamente eliminados.
Seguridad certificada
iShredder™ Android está oficialmente certificado DEKRA MASA L1, cumpliendo con los estrictos estándares OWASP para protección de datos y seguridad en aplicaciones móviles. Borra datos sensibles con confianza, usando una app verificada de forma independiente como libre de vulnerabilidades.
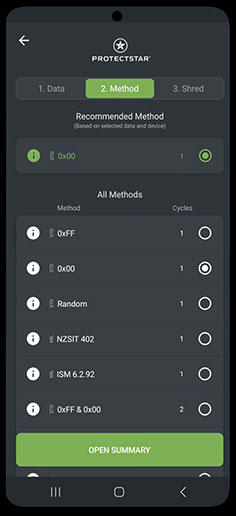
Algoritmos de eliminación certificados
Con más de 20 algoritmos de eliminación aprobados, iShredder™ supera incluso los estándares internacionales de seguridad gubernamentales y militares para la eliminación segura de datos. Además, las autoridades y organizaciones independientes han analizado cada método de eliminación por su seguridad y para garantizar una destrucción de datos segura.
Dependiendo de la edición utilizada, están disponibles algoritmos de eliminación como DoD 5220.22-M E, U.S. Air Force (AFSSI-5020), U.S. Army AR380-19, DoD 5220.22-M ECE, BSI/VS-ITR TL-03423 Standard, BSI-2011-VS, BSI TL-03423, NATO Standard, CSEC ITSG-06, HMG InfoSec No.5, DoD 5220.22 SSD y otros.
Desarrollado específicamente por Protectstar™ Inc. en 2007, pasa por cincuenta rutinas de eliminación.
Los datos se sobrescriben dos veces con un valor aleatorio, luego con sus complementos. Incluye el estándar DoD 5220.22-M (E) y el método de Peter Gutmann y algoritmos aleatorios.
El algoritmo de Peter Gutmann fue desarrollado en 1996 y realiza 35 pasadas de sobrescritura en total.
Este algoritmo es uno de los métodos más avanzados para la destrucción de datos.
En marzo de 2010, la Oficina Federal de Seguridad Informática de Alemania (BSI) publicó una nueva directriz técnica para "Requisitos para sobrescribir medios de memoria".
El método es similar al estándar VSITR para medios de almacenamiento magnéticos.
En total, el nuevo algoritmo tiene 8 ciclos, que deben ejecutarse en orden cronológico. Incluye un ciclo de verificación.
El método de la OTAN es el estándar de eliminación de la Organización del Tratado del Atlántico Norte (OTAN).
Sobrescribirá el área de datos objetivo 7 veces.
Las primeras seis sobrescrituras son con valores fijos (0x00) y (0xff), alternando entre pasadas.
La 7ª sobrescritura es con un valor aleatorio, es decir, 0x00, 0xFF, 0x00, 0xFF, 0x00, 0xFF y la 7ª pasada con un valor aleatorio.
El método de alta seguridad se basa en el 'Manual de Operación del Programa de Seguridad Industrial Nacional' de enero de 1995 por el Departamento de Defensa (DoD).
En esta variación de siete ciclos (DoD 5220.22-M ECE), los datos se sobrescriben primero tres veces con los estándares DoD 5220.22-M (E), luego con un valor aleatorio específico, y finalmente una vez más con DoD 5220.22-M (E).
El estándar de la Real Policía Montada de Canadá RCMP TSSIT OPS-II sobrescribe los datos de forma segura con secuencias alternas en un total de siete ciclos.
La Oficina Federal de Seguridad Informática de Alemania (BSI) describe en la directriz técnica BSI-2011 los 'Requisitos para sobrescribir medios de memoria' de julio de 2010.
Esta cláusula incluye 5 pasos, que se implementan en orden secuencial.
Este método está especialmente desarrollado para SSD (Unidad de Estado Sólido) y memoria flash, basado en el estándar DoD 5220.22-M E del Departamento de Defensa de EE.UU. Sobrescribe los datos cuatro veces.
Este método está especialmente desarrollado para SSD (Unidad de Estado Sólido) y memoria flash, basado en el estándar DoD 5220.22-M E del Departamento de Defensa de EE.UU. Sobrescribe los datos cuatro veces.
El método de sanitización CSEC ITSG-06 canadiense tiene tres ciclos y fue publicado en 2006 por el Establecimiento de Seguridad de las Comunicaciones de Canadá (CSEC).
El estándar HMG Infosec No 5 - nivel mejorado está aprobado para borrar datos Top Secret del gobierno del Reino Unido y también ha sido aprobado por la OTAN.
El algoritmo es un algoritmo de sobrescritura de tres pasadas: primera pasada con ceros (0), segunda y tercera pasadas con su complemento y valores aleatorios (con verificación en la última pasada).
El método de sanitización AFSSI-5020 fue definido originalmente en la Instrucción de Seguridad de Sistemas de la Fuerza Aérea 5020 por la Fuerza Aérea de los Estados Unidos (USAF) en 1996 y puede seguir usándose hoy en día.
Este es el estándar de la Marina de los EE.UU. NAVSO P-5239-26 para discos codificados MFM.
Este método de eliminación primero escribe el valor fijo (0xffffffff) en el área de datos objetivo, luego el valor fijo (0xbfffffff) y luego valores aleatorios.
Finalmente, el área de datos objetivo se lee para verificar las sobrescrituras.
Este es el estándar de la Marina de los EE.UU. NAVSO P-5239-26 para discos codificados RLL.
Este método de eliminación primero escribe el valor fijo (0xffffffff) en el área de datos objetivo, luego el valor fijo (0x27ffffff) y luego valores aleatorios.
Finalmente, el área de datos objetivo se lee para verificar las sobrescrituras.
AR380-19 es el algoritmo de trituración de datos especificado y publicado por el Ejército de los EE.UU.
El algoritmo es un algoritmo de sobrescritura de tres pasadas: primera pasada con bytes aleatorios, segunda y tercera pasadas con ciertos bytes y con su complemento (con verificación en la última pasada).
El método de baja seguridad pero alta velocidad de ejecución se basa en el 'Manual de Operación del Programa de Seguridad Industrial Nacional' de enero de 1995 del DoD (DoD de EE. UU. 5220.22-M).
La variación (DoD 5220.22-M E) ofrece 3 ciclos en los que los datos se sobrescriben primero con un valor fijo, luego su complemento, y luego un valor aleatorio.
El estándar estadounidense NCSC-TG-025 del National Computer Security Center (NCSC) sobrescribe de forma segura la información existente en un medio de datos tres veces.
El estándar publicado en 2006 es la Publicación Especial 800-88 de NIST, que es el estándar de eliminación de datos más utilizado para organizaciones en los Estados Unidos. Sus principios se aplican a tecnologías de almacenamiento magnético, basadas en flash y otras, desde unidades USB hasta servidores.
El estándar ruso de eliminación de datos GOST R 50739-95 para eliminación segura de datos sobrescribe el área de datos objetivo dos veces. En la primera pasada con ceros y en la segunda pasada con caracteres aleatorios.
ISM 6.2.92 es el estándar de sanitización de datos del gobierno australiano.
El método fue definido originalmente en el Manual de Seguridad de la Información (ISM) emitido por el Departamento de Defensa de Australia: Inteligencia y Seguridad.
La sanitización ISM 6.2.92 no puede usarse para sanitizar información clasificada.
Este método está especialmente desarrollado para SSD (Unidad de Estado Sólido) y memoria flash.
Ofrece un ciclo en el que los datos se sobrescriben con el patrón "0xFF".
Este método para seguridad más baja pero con una velocidad de ejecución muy alta. Ofrece solo un ciclo en el que los datos se sobrescriben con valores aleatorios.
En diciembre de 2014, las directrices fueron revisadas, convirtiendo la versión actual en “NIST Special Publication 800-88 Rev. 1”.
Vea aquí la descripción del método que ha seleccionado.
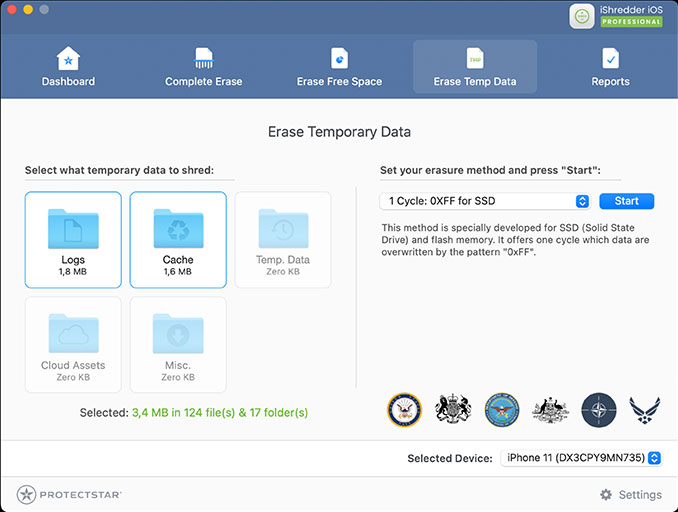
Limpieza de datos temporales
Lo que mucha gente pasa por alto son los cachés del navegador, archivos de registro y otros almacenamientos temporales. iShredder™ limpia también estas áreas, dándote más espacio libre y protegiendo tu privacidad.
Quieres vender tu dispositivo
¿Riesgo de seguridad desconocido? ¡No gracias!
Siempre que revendas un smartphone, laptop o tablet, normalmente quedará un rastro digital de tus datos personales. iShredder™ elimina irreversible esos rastros, asegurando que nadie extraño pueda acceder a fotos, contraseñas o documentos. Esto significa que puedes entregar o vender tu dispositivo con total tranquilidad.
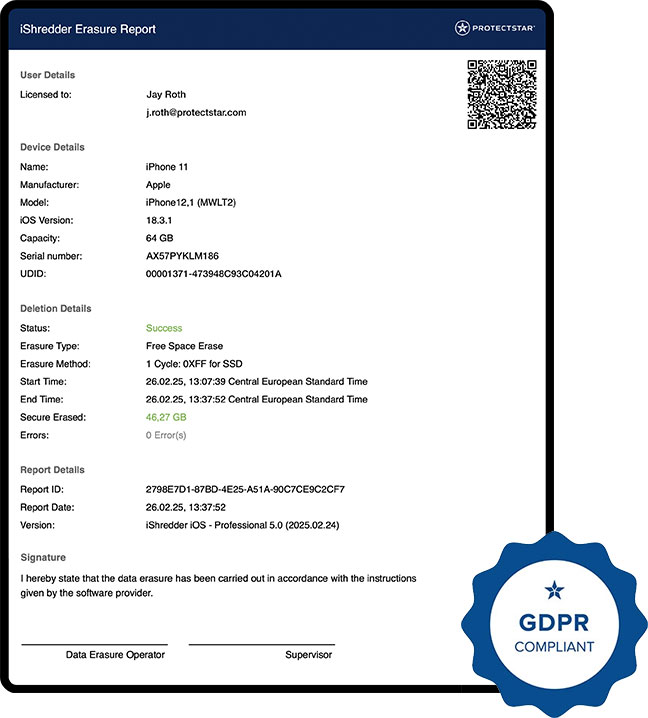
100% de confianza: Informes detallados de eliminación
Después de cada acción de eliminación, iShredder™ genera un informe detallado con una marca de tiempo, lista de archivos y el algoritmo utilizado. Esto es tu prueba de que los datos realmente se han ido — ideal para empresas que necesitan cumplimiento con el GDPR (o el estándar InfoSec No. 5 del gobierno del Reino Unido, DoD de EE. UU., NIST 800-88) o para usuarios privados que exigen seguridad de primer nivel.
Lo que la gente dice de nosotros

4M+
Descargas
Confíe en iShredder™ — el #1
en Borrado Seguro de Datos.
Descargue iShredder™ gratis ahora, o elija la edición (Gratis, Pro, Militar, GOV) que mejor se adapte a sus necesidades.
Disfrute de protección de borrado de grado militar sin configuraciones complicadas.




GRATIS
Ideal para nuevos usuarios que desean familiarizarse con las aplicaciones
-
Sobrescribir de manera segura el espacio libre
-
Borrado seguro del espacio libre en la tarjeta SD
-
Algoritmos estándar de eliminación preinstalados
-
Métodos de borrado en total: 4
-
Crear y exportar informes de borrado
PRO
Ideal para usuarios que desean funciones más avanzadas
-
Sobrescribir de manera segura el espacio libre
-
Borrado seguro del espacio libre en la tarjeta SD
-
Algoritmos estándar de eliminación preinstalados
-
Métodos de borrado en total: 14
-
Borrado seguro de la tarjeta SD
-
Borrado seguro de unidades USB externas, discos duros, etc.
-
Eliminación segura de archivos y carpetas
-
Eliminación segura de archivos multimedia
-
Eliminación segura de contactos y portapapeles
-
Crear y exportar informes de borrado
MILITAR
Ideal para usuarios que desean funciones de grado militar
-
Sobrescribir de manera segura el espacio libre
-
Borrado seguro del espacio libre en la tarjeta SD
-
Algoritmos estándar de eliminación preinstalados
-
Métodos de borrado en total: 25
-
Borrado seguro de la tarjeta SD
-
Borrado seguro de unidades USB externas, discos duros, etc.
-
Eliminación segura de archivos y carpetas
-
Eliminación segura de archivos multimedia
-
Eliminación segura de contactos y portapapeles
-
Métodos adicionales de eliminación de grado militar y empresarial
-
Establecer el método de eliminación predeterminado
-
Protección con contraseña
-
Crear y exportar informes de borrado
GOV
Ideal para expertos que desean tener todos los beneficios
-
Sobrescribir de manera segura el espacio libre
-
Borrado seguro del espacio libre en la tarjeta SD
-
Algoritmos estándar de eliminación preinstalados
-
Métodos de borrado en total: 25
-
Borrado seguro de la tarjeta SD
-
Borrado seguro de unidades USB externas, discos duros, etc.
-
Eliminación segura de archivos y carpetas
-
Eliminación segura de archivos multimedia
-
Eliminación segura de contactos y portapapeles
-
Eliminación segura de SMS, MMS y registros de llamadas
-
Métodos adicionales de eliminación de grado militar y empresarial
-
Establecer el método de eliminación predeterminado
-
Protección con contraseña
-
Crear y exportar informes de borrado
PRO
Ideal para usuarios que desean funciones más avanzadas
-
Borrado seguro de archivos, carpetas y particiones
-
Corte y pegado seguro de archivos y directorios
-
Borrado seguro de dispositivos externos
-
Asistente inteligente de borrado seguro
-
Borrado seguro de archivos temporales de Windows
-
Borrado seguro de archivos temporales de internet
-
Registros avanzados de eliminación
-
Algoritmos de borrado seguros especiales para SSD y memoria flash
-
Algoritmo de eliminación segura Protectstar™
-
Destruidor de datos para unidades de estado sólido
-
Soporte técnico durante 1 año
-
11 métodos de borrado en total
MILITAR
Ideal para usuarios que desean funciones de grado militar
-
Borrado seguro de archivos, carpetas y particiones
-
Corte y pegado seguro de archivos y directorios
-
Borrado seguro de dispositivos externos
-
Asistente inteligente de borrado seguro
-
Borrado seguro de archivos temporales de Windows
-
Borrado seguro de archivos temporales de internet
-
Registros avanzados de eliminación
-
Algoritmos de borrado seguros especiales para SSD y memoria flash
-
Algoritmo de eliminación segura Protectstar™
-
Destruidor de datos para unidades de estado sólido
-
Métodos de eliminación militar mejorados como el estándar de la OTAN, el NAVSO P-5239-26 de la US Navy, el USAF AFSSI-5020 y el CSEC ITSG-06.
-
Soporte técnico durante 1 año
-
18 métodos de borrado en total
PRO
Ideal para usuarios que desean funciones más avanzadas
-
Compatible con todos los modelos de MacBook, MacBook Air, Macbook Pro, iMac, iMac Pro y Mac Pro
-
Eliminación de datos hasta el nivel de seguridad de alto secreto
-
Algoritmos de eliminación como DoD 5220.22-M ECE, Peter Gutmann, DoD 5220.22-M, HMG Infosec No.5, BSI alemán-2011-VS, US Army AR380-19 y más
-
Informe detallado de borrado proporciona evidencia de eliminación
-
Compatible con unidades de estado sólido (SSD) y memoria flash
-
Soporte completo de arrastrar y soltar
-
Métodos de borrado en total (11)
-
Incluye soporte técnico por 1 año y actualizaciones gratuitas
-
Soporte 24/7 por correo electrónico
MILITAR
Ideal para usuarios que desean funciones de grado militar
-
Compatible con todos los modelos de MacBook, MacBook Air, Macbook Pro, iMac, iMac Pro y Mac Pro
-
Eliminación de datos hasta el nivel de seguridad de alto secreto
-
Algoritmos de eliminación como DoD 5220.22-M ECE, Peter Gutmann, DoD 5220.22-M, HMG Infosec No.5, BSI alemán-2011-VS, US Army AR380-19 y más
-
Informe detallado de borrado proporciona evidencia de eliminación
-
Compatible con unidades de estado sólido (SSD) y memoria flash
-
Soporte completo de arrastrar y soltar
-
Informes avanzados de eliminación
-
Métodos de eliminación militar mejorados como el estándar de la OTAN, US Navy NAVSO P-5239-26 (MFM & RLL), USAF AFSSI-5020, BSI TL-03423 y CSEC ITSG-06
-
Métodos de borrado en total (21)
-
Incluye soporte técnico por 1 año y actualizaciones gratuitas
-
Soporte 24/7 por correo electrónico
PRO
Ideal para usuarios que desean funciones más avanzadas
-
Compatible con todos los modelos de iPhone®, iPad® y iPod® touch
-
Compatible con todas las versiones de iOS®
-
Sobrescribir de manera segura el espacio libre
-
Borrado completo de todos los datos en el dispositivo iOS®
-
Limpieza segura de datos temporales
-
Incluye soporte técnico por 1 año y actualizaciones gratuitas
-
Informes avanzados de eliminación
-
Soporte 24/7 por correo electrónico
-
Métodos de borrado en total (11)
-
Algoritmo de Eliminación Segura Avanzada Protectstar™ (2017)
MILITAR
Ideal para usuarios que desean funciones de grado militar
-
Compatible con todos los modelos de iPhone®, iPad® y iPod® touch
-
Compatible con todas las versiones de iOS®
-
Sobrescribir de manera segura el espacio libre
-
Borrado completo de todos los datos en el dispositivo iOS®
-
Limpieza segura de datos temporales
-
Incluye soporte técnico por 1 año y actualizaciones gratuitas
-
Informes avanzados de eliminación
-
Explorador de Archivos Seguro Integrado
-
Borrado seguro de AppleTV (todos los modelos)
-
Soporte 24/7 por correo electrónico
-
Métodos de borrado en total (18)
-
Algoritmo de Eliminación Segura Avanzada Protectstar™ (2017)
-
Método de borrado de 50 ciclos Protectstar™ Secure Deletion Algorithm®







