Featured in:

What is iShredder™?
iShredder™ is the most popular data eraser for iOS, Android, Windows, Mac, and Windows Server. Since 2010, this secure deletion software has won numerous awards and is used by more than 5,000,000 users in over 100 countries worldwide.
iShredder™ uses data shredding techniques that go beyond international standards. Moreover, its data deletion is so secure that government agencies and defense ministries trust and use this robust process.
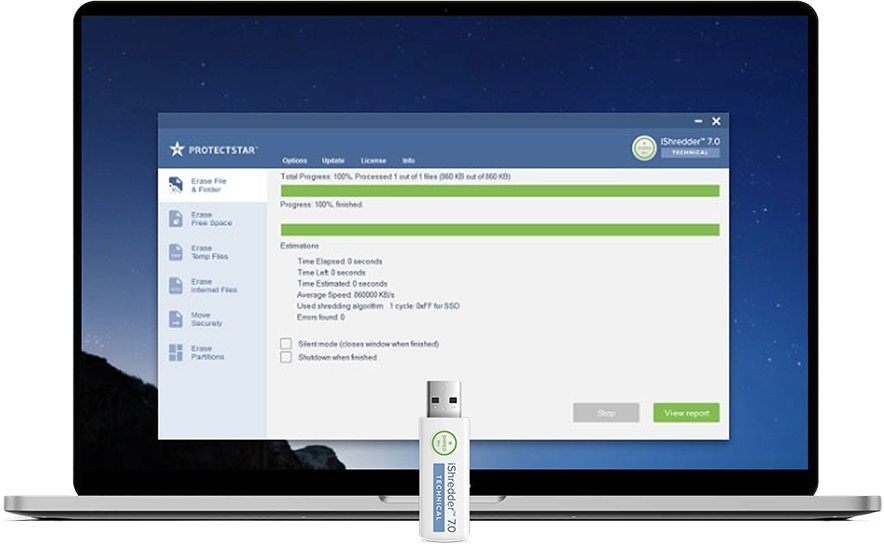
Secure Erasing of Confidential DataiShredder™ is a state-of-the-art and professional tool that has won numerous awards and that allows for secure deletion of data from hard drives and external data storage devices. This user-friendly solution, which runs under Microsoft Windows, enables users to efficiently delete their data in such a way as to preclude reconstruction, even by government agencies.
iShredder™ is a state-of-the-art and professional tool that has won numerous awards and that allows for secure deletion of data from hard drives and external data storage devices. This user-friendly solution, which runs under Microsoft Windows, enables users to efficiently delete their data in such a way as to preclude reconstruction, even by government agencies.
Special features

 Secure data deletion based on government approved and military data security standards up to the confidential, secret and top secret security standard levels
Secure data deletion based on government approved and military data security standards up to the confidential, secret and top secret security standard levels Integration of the powerful Protectstar™ Secure Deletion Algorithm© allows for fail-safe data security
Integration of the powerful Protectstar™ Secure Deletion Algorithm© allows for fail-safe data security Detailed deletion log provides evidence of deletion
Detailed deletion log provides evidence of deletion Supports IDE/ATA, SCSI, USB, SATA, SAS, RAID, Firewire
Supports IDE/ATA, SCSI, USB, SATA, SAS, RAID, Firewire Compatible with Solid State Drives (SSD)
Compatible with Solid State Drives (SSD) Deletes confidential data from hard drives, solid state drive, memory sticks, usb sticks, flash drives, CompactFlash, Secure Digital (SD) card, memory cards, MMC, xD, MicroDrive, etc
Deletes confidential data from hard drives, solid state drive, memory sticks, usb sticks, flash drives, CompactFlash, Secure Digital (SD) card, memory cards, MMC, xD, MicroDrive, etc System partitions and individual system drives can be deleted securely in offline mode without a boot medium
System partitions and individual system drives can be deleted securely in offline mode without a boot medium Allows for secure cutting and pasting of files and directories
Allows for secure cutting and pasting of files and directories 1-year technical support and free updates and upgrades
1-year technical support and free updates and upgrades Supports FAT, FAT32 and NTFS
Supports FAT, FAT32 and NTFSMore than TWENTY methods of erasure
In a sector where trust and security are primary concerns, Protectstar™ provides its customers with only modern and first-class products. iShredder™ Windows offers more than twenty secure deletion methods certified by the government and military organizations.
Erasure Algorithm:
- 50 Cycles: Protectstar SDA (2007)
- 35 Cycles: Gutmann method
- 8 Cycles: German BSI TL-03423
- 7 Cycles: NATO Standard
- 7 Cycles: DoD 5220.22-M ECE
- 7 Cycles: CANADIAN RCMP TSSIT OPS-II
- 5 Cycles: BSI-2011-VS
- 4 Cycles: Protectstar ASDA (2017)
- 4 Cycles: DoD 5220.22-M E for SSD
- 3 Cycles: Canadian CSEC ITSG-06
- 3 Cycles: HMG Nr. 5 extended
- 3 Cycles: AFSSI-5020
- 3 Cycles: NAVSO P-5239-26 (MFM)
- 3 Cycles: NAVSO P-5239-26 (RLL)
- 3 Cycles: US Army AR380-19
- 3 Cycles: DoD 5220.22-M E
- 3 Cycles: NCSC-TG-025
- 3 Cycles: NIST SP 800-88
- 2 Cycles: RUSSIAN GOST R 50739-95
- 1 Cycle: Australian ISM 6.2.92
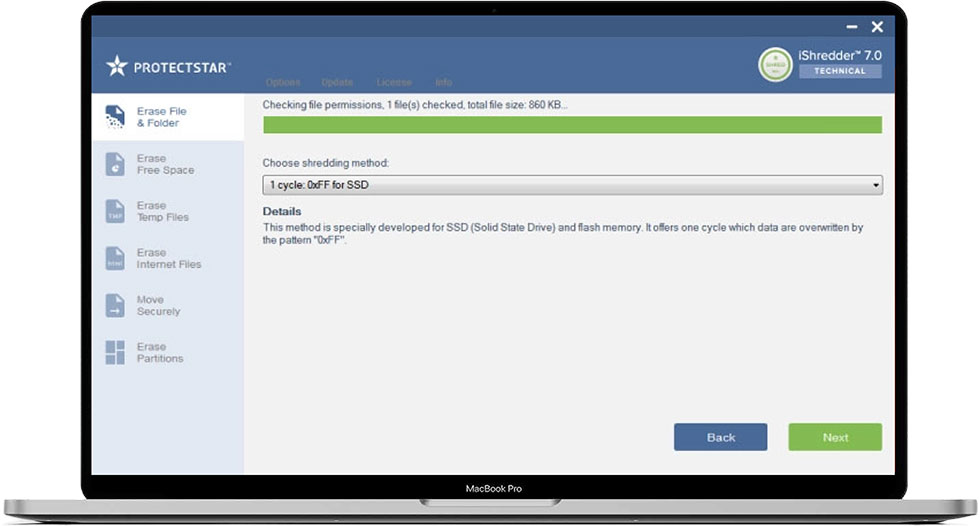
- 1 Cycle: 0XFF for SSD
- 1 Cycle: Random Values
- 1 Cycle: NIST SP 800-88 Rev. 1 (2014)

Specifically developed by Protectstar™ Inc. in 2007 it runs through fifty erasure routines.
Data will be overwritten for two times with a random value, afterwards with their complements. It includes the DoD 5220.22-M (E) standard and Peter Gutmann method and random algorithms.
The algorithm from Peter Gutmann was found in 1996 and makes 35 overwrite passes in total.
This algorithm is one of the state-of-the-art methods for data destruction.
In March 2010 the German Federal office for IT Security (BSI) published a new technical BSI Guideline for "Requirements to overwrite memory media".
The method is similar to VSITR standard for magnetic storage media.
In total the new algorithm has 8 cycles, which has to be worked through in chronological order. Includes one cycle of verification.
The NATO method is the deletion standard of North Atlantic Treaty Organization (NATO).
It will overwrite the target data area 7 times.
The first six overwrites are with the fixed values (0x00) and (0xff), alternating between passes.
The 7th overwrite is with a random value i.e. 0x00,0xFF,0x00,0xFF,0x00,0xFF and 7th pass with a random value.
The method for high security is based on the January 1995 'National Industrial Security Program Operating Manual'by the Department of Defense (DoD).
In this seven cycle variation (DoD 5220.22-M ECE), data is first overwritten three times with DoD 5220.22-M (E) Standards, then with a specific random value, and finally once again with DoD 5220.22-M (E).
The Royal Canadian Mounted Police Standard RCMP TSSIT OPS-II overwrites data securely with alternating sequences with a total of seven cycles.
The German Federal office for IT Security (BSI) describes in the technical BSI guideline for 'Requirements to overwrite memory media' from July 2010 the modern method BSI-2011.
This clause includes 5 steps, which is implemented in sequential order.
ASDA enables highly effective, verifiable data erasure with minimal resource consumption. The four passes are designed for efficiency and transparency: read‑after‑write verification and deletion logs document every step. AES‑256 and cryptographically strong random numbers make forensic reconstruction significantly harder. The implementation integrates seamlessly into existing processes.
This method is specially developed for SSD (Solid State Drive) and flash memory, based on the U.S.
Department of Defense's standard DoD 5220.22-M E. It will overwrite data four times.
The Canadian CSEC ITSG-06 sanitization method has three cycles and was published in 2006 by Communication Security Establishment Canada (CSEC).
The HMG Infosec Standard No 5 - enhanced level is approved to wipe UK Government Top Secret data and has also been approved by NATO.
The algorithm is a three pass overwriting algorithm: first pass - with zeros (0), second and third passes with its complement and random values(with last pass verification).
The AFSSI-5020 sanitization method was originally defined in the Air Force System Security Instruction 5020 by the United States Air Force (USAF) in 1996 and may still be today.
This is the US Navy standard NAVSO P-5239-26 for MFM encoded drives.
This deletion method first writes the fixed value (0xffffffff) to the target data area, then the fixed value (0xbfffffff) and then random values.
Finally, the target data area is read to verify the overwrites.
This is the US Navy standard NAVSO P-5239-26 for RLL encoded drives.
This deletion method first writes the fixed value (0xffffffff) to the target data area, then the fixed value (0x27ffffff) and then random values.
Finally, the target data area is read to verify the overwrites.
AR380-19 is the data shredding algorithm specified and published by the U.S. Army.
The algorithm is a three pass overwriting algorithm: first pass - with random bytes, second and third passes with certain bytes and with its complement (with last pass verification).
The method for low security but for high execution speed is based on the January 1995 'National Industry Security Program Operating Manual' from the DoD (US DoD 5220.22-M).
The variation (DoD 5220.22-M E) offers 3 cycles in which the data are overwritten with first a set value, then its complement , and then a random value.
The American NCSC-TG-025 standard of the National Computer Security Center (NCSC) securely overwrites existing information on a data medium three times.
The in 2006 released standard is the Special Publication 800-88 from NIST, which is the go-to data erasure standard for organizations in the United States. Its principles can apply to magnetic, flash-based, and other storage technologies, from USB drives to servers.
The Russian data deletion standard GOST R 50739-95 for secure data erasure overwrites the target data area two times. In the first pass with a zero, and in the second pass with random characters.
ISM 6.2.92 is the Australian government's data sanitization standard.
The method was originally defined in the Information Security Manual (ISM) issued by the Australian Department of Defense: Intelligence & Security.
The ISM 6.2.92 sanitization cannot be used to sanitize classified information.
This method is specially developed for SSD (Solid State Drive) and flash memory.
It offers one cycle which data are overwritten by the pattern "0xFF".
This method for lowest security but for very high execution on speed. It offers only one cycle which data are overwritten with random values.
In December 2014, the guidelines were revised, making the current version “NIST Special Publication 800-88 Rev. 1”.
See here the description of the method you have selected.

Certified Algorithms & Detailed Reports
With over 20 recognized erasure algorithms, iShredder™ exceeds international government and military security standards for secure data erasure. Each method — such as DoD 5220.22-M E/ECE, NIST SP 800-88, and BSI-2011-VS — has been vetted by government agencies or independent organizations, ensuring permanent data destruction. Upon completion of each wipe, iShredder™ automatically generates a detailed erasure report to confirm compliance with data protection regulations.

GDPR/DSGVO-Compliant Data Erasure
The European General Data Protection Regulation (EU-DSGVO) has made secure, documented data erasure a legal requirement for all organizations. Should sensitive information be mishandled, businesses risk fines, legal consequences, and reputational damage. iShredder™ fully complies with DSGVO (GDPR) guidelines, including the “Right to Erasure” (Art. 17, GDPR-info.eu), by providing digitally signed reports that confirm complete data destruction.
Benefits of | Professional | Military | ProfeServerssional | Military Server | Technical | |
|---|---|---|---|---|---|---|
| Secure erase of files, folders and partitions | ||||||
| Secure cutting and pasting of files and directories | ||||||
| Secure erase of external devices | ||||||
| Smart secure erase wizard | ||||||
| Secure erase of temporary Windows files | ||||||
| Secure erase of temporary internet files | ||||||
| Advanced deletion logs | ||||||
| Preinstalled secure erasing methods like DoD 5220.22-M, HMG Infosec No.5, German BSI-2011-VS, US Army AR380-19 and more. | ||||||
| Additional secure erasing methods like DoD 5220.22-M ECE, Peter Gutmann | ||||||
| Special secure wiping algorithms for SSD & flash memory | ||||||
| Protectstar™ Secure Deletion Algorithm | ||||||
| Enhanced military deletion methods like NATO standard, US Navy NAVSO P-5239-26 , USAF AFSSI-5020 and CSEC ITSG-06. | ||||||
| 1 Year technical support | ||||||
| Erasing methods in total | 11 | 18 | 11 | 18 | 18 | |
| Windows Server compatible | ||||||
| Boot from USB stick |

Purchase iShredder™ 7 with Care Plan get 3 years premium support
All iShredder™ products come with a 12-months professional service and free updates and upgrades.
To extend your maintenance support further, purchase a Care Plan.
The Care Plan gives you 36-months premium support and free upgrades to new versions for the next three years.
Premium technical support
3 years free updates and upgrades
Best value for your money
iShredder™ Windows
Technical Edition

Secure erase of files, folders and partitions
Secure cutting and pasting of files and directories
Secure erase of external devices
Smart secure erase wizard
Secure erase of temporary Windows files
Secure erase of temporary internet files
Advanced deletion logs
Special secure wiping algorithms for SSD & flash memory
Protectstar™ Secure Deletion Algorithm
Data Shredder for Solid State Drives
Enhanced military deletion methods like NATO standard, US Navy NAVSO P-5239-26 , USAF AFSSI-5020 and CSEC ITSG-06.
1 Year technical support
18 erasing methods in total
Windows Server compatible