Guiding Principle
Our mission is simple: protect information before it becomes a liability.
For more than twenty years, we’ve built solutions that work when it matters with no cloud dependency and auditable proof for inspections. Minimal. Rugged. Reliable.
Four Commitments
Fast. Built‑in presets: NIST 800‑88, IEEE 2883‑2022, BSI‑CON.6.
Offline. Air‑gapped, field‑ready, no telemetry.
Auditable. Verified processes, signable reports.
Scalable. From a single depot drive to entire fleets.
iShredder™ Defense for Drones
Mission data is valuable but dangerous in the wrong hands.
iShredder™ Defense for Drones renders it irreversibly unusable: fast, standards‑aligned, with auditable proof.
Status: In development. Not available for purchase
Early Access: Join the waitlist. We prioritize units ready for evaluation.
Why this solution stands out
Mission‑ready presets:
NIST 800‑88 (Clear/Purge/Destroy) · IEEE 2883‑2022 · BSI‑CON.6 · DoD 5220.22‑M / HMG IS5 (legacy compatibility).
NSA/CSS 9‑12 is presented as a destruction workflow (with EPL reference).
Broad coverage:
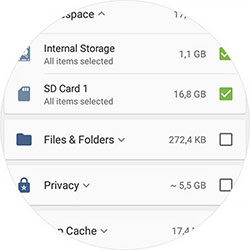
Secure erasure of HDD/SSD, removable media, and memory cards; support for NVMe Sanitize, ATA Secure Erase/Enhanced, SCSI SANITIZE, eMMC Secure Erase/Trim, SD‑ERASE.
Proof included:
Digitally signable erasure reports with method, LBA coverage (incl. HPA/DCO/OP), timestamps, and device IDs. Ideal for chain‑of‑custody and audits.
Platforms
Windows, macOS, iOS and Android. Built for depot workstations and controller tablets.
How it works in the depot
(Windows/macOS)
iShredder™ operates fully offline and prioritizes hardware‑level purge commands — such as NVMe Sanitize, ATA Secure Erase/Enhanced, SCSI SANITIZE, eMMC Secure Erase/Trim, or SD‑ERASE. It then verifies LBA coverage (including HPA/DCO/OP). The report includes method, timestamps, and device IDs for chain‑of‑custody.
For random‑pattern overwrites, iShredder™ uses a cryptographically secure RNG (e.g., NIST SP 800‑90A DRBG). Optional FIPS 140‑3‑capable builds with CAVP‑validated DRBGs are available; formal validation will be listed by certificate ID.
-
![Connect]()
Connect
Attach the mission SSD/HDD or card via a verified adapter or service port.
-
-
![Select profile]()
Select profile
Choose the classification profile (e.g., NIST Purge / IEEE 2883 Purge / BSI profile).
-
-
![Erase & attest]()
Erase & attest
iShredder performs the appropriate sanitize/crypto‑erase or verified overwrite and generates a digitally signable erasure report.
Standards & Guidelines
In the U.S./DoD, NIST SP 800‑88 Rev. 1 is the baseline (Clear/Purge). For classified media, NSA/CSS 9‑12 applies; approved destruction devices are listed on the EPL. In Germany/EU, practice follows BSI IT‑Grundschutz CON.6, selecting the method by protection needs - for SSDs, device‑/command‑specific sanitization is preferred. In the UK, see NCSC “Secure sanitisation of storage media.” In the NATO context, the NATO Security Policy sets the guardrails; specific erasure patterns are defined nationally.
Preset recommendation:
- Unclassified/FOUO:NIST/IEEE Clear
- Sensitive/Secret:NIST/IEEE Purge (e.g., NVMe Sanitize / ATA Secure Erase) + verification
- Top Secret / NATO Secret:Destruction workflow per NSA/CSS 9‑12/EPL or national guidance